The BuildAssure Verify Utility is a command-line executable that runs in a user-initiated command prompt window. It supports the following commands:
SCANSYSTEM: Scans the platform to retrieve current platform values and outputs them to the console. This command does not involve file input or output.
READFILE: Reads the Direct Platform Data file specified by the -in file option and outputs the values to the console. The Build Assure Issuing CA file is specified by the -ca file option. Only one input file is used.
SCANREADCOMP: Scans the platform for current values, reads the Direct Platform Data file specified by the -in option. The BuildAssure Issuing CA file is specified by the -ca option. It compares the platform values with the file values and outputs the comparison to the console. If the -fl flag is included, the comparison results are written to the specified output file.
PFORMCRTCOMP: Compares the contents of the signed Platform Attribute Certificate file specified by the –in command line option to the current information from the system. It detects changes in elements like the EK Serial Number from the Trusted Platform Module and the Platform Serial Number in the system. It also compares the platform configuration from the file against the current components from the system.
The results of the comparison will be displayed in the console. The command will indicate whether changes were detected at system or component level as warning messages (in yellow). If the result of the comparison is successful, then a success message will be displayed saying PFORMCRTCOMP PASS. If it is not successful, then it will display PFORMCRTCOMP FAIL. It will also show the differences line by line in red.
WRITEDELTAFILE: Allows to generate new delta xml file that will include only the platform components that have been either added, modified or removed from the original system setup. It will perform a comparison of all the platform components based on current platform information by taking as input the base platform attribute certificate file and optionally passing a list of previous delta attribute certificates files.
CASIGVERIFY: Verifies the signature of the TSC Issuing CA file. Optionally, it can also verify the signature of either a signed Platform Attribute Certificate or a signed Direct Platform Data File using the public key of the TSC Issuing CA certificate. The TSC Issuing CA file is specified by the –ca file option. The signed Platform Attribute Certificate or signed Direct Platform Data File can be specified by the –in option. The CASIGVERIFY command will only verify one file at a time.
The following is the command line syntax for the commands and options:
Syntax : TSCVerifyTool SCANSYSTEM | READFILE | SCANREADCOMP | PFORMCRTCOMP | WRITEDELTAFILE | CASIGVERIFY Options
Commands:
SCANSYSTEM | option allows user to scan the system configurations. |
READFILE | option allows user to read the content of the digital-signed DPD file. |
SCANREADCOMP | option allows user to compare the DPD snapshot against the runtime system configurations. |
PFORMCRTCOMP | option allows user to verify the platform certificate contents & signature. |
CASIGVERIFY | option allows user to verify the signature of the platform certificate. |
WRITEDELTAFILE | option allows user to generate a Delta Certificate of the changes since the Platform Certificate was signed. |
Optional -in|/in (in file) | flag specified the filename of the read file. |
Optional -ca|/ca (in issuing CA) | flag specified the filename of the issuing CA file. |
Optional -fl|/fl (out file) | flag specifies the filename of the Platform Component Compare |
Optional -vl|/vl | flag to turn on verbose messages. |
Optional -deltas|/deltas | flag allows user to specify a list of delta input files. All files must exist. |
Optional -notpm |/notpm | flag to skip collecting the TPM information on the system or board. |
Optional -nohdd |/nohdd | flag to skip collecting hard drive data on the system or board. |
Optional -noamt |/noamt | flag to allow user to collect DPD on non-TPM system or board. |
Optional -ecc |/ecc | flag to specify collecting the TPM ECC EK Certificate. |
Optional -server |/server | flag to support collecting server features: BMC, FRU, SDR, etc. |
Optional -dsg |/dsg | flag to support collecting DSG server configurations
|
Verify Utility Status Return Value
The Build Assure Verify Utility will return an integer value for pass and fail: Return values: 0 – PASS, 1 – FAIL.
Scan System Command
SCANSYSTEM – Scans the platform to retrieve the current platform values and outputs the component data to the console. No input or output files are involved.
The scan performs the following operations:
- Reads the System BIOS DMI Tables for information on the BIOS, System, Motherboard, Chassis, Processor, Memory, Security/AMT, Power Supplies, and Batteries.
- Reads the Trusted Platform Module (TPM) PCR Registers, Public Endorsement Key, and Endorsement Key Serial Number.
- Retrieves Drive Information (Note: Removable drives will not be scanned).
Read File Command
READFILE - Reads the Direct Platform Data file specified by the file selected -in filename. The platform component information in the DPD file is directed to the console output.

The Direct Platform Data file is a signed XML file. Once the DPD file is read, the XML signature is verified against the Build Assure Issuing CA.
If the XML signature of the DPD file does not match, the following error message will be displayed:
Direct Platform Data file: DPD_Filename.xml - XML file signature does not match.
Scan System Read File Compare
SCANREADCOMP – Scans the platform components and reads the Direct Platform Data file specified by the file selected -in filename. The component change information is directed to the console output. If the -fl option is selected, then the Platform Component Change data file is generated with the results of the compare as the output.
Upon completion of the comparison operation, the results will be displayed. If the comparison results match, the following message will be shown:
10 components scanned
No component changes have been detected
Compare Results = 0
If changes are detected, the output will display the details of these changes.
The changes between the System Snapshot data and the Direct Platform Data are displayed side by side. Any Component Data changes are displayed in red.
10 components scanned
1 component change has been detected
Compare Results = 1
After the comparison is completed, a Platform Component Compare Data XML file is generated.
- If the -fl option is provided, it allows customization of the file name.
- If the -fl option is not provided, the tool generates the file using a default filename.
Upon completing the comparison operation, a Platform Component Compare Data file is generated. If the comparison results match, the file will indicate that the results are true.
Component Changes
If the comparison operation detects changes, the Data file will indicate that the comparison results are false and list the components that have changed.
The XML schema for the Platform Component Compare data file is as follows:
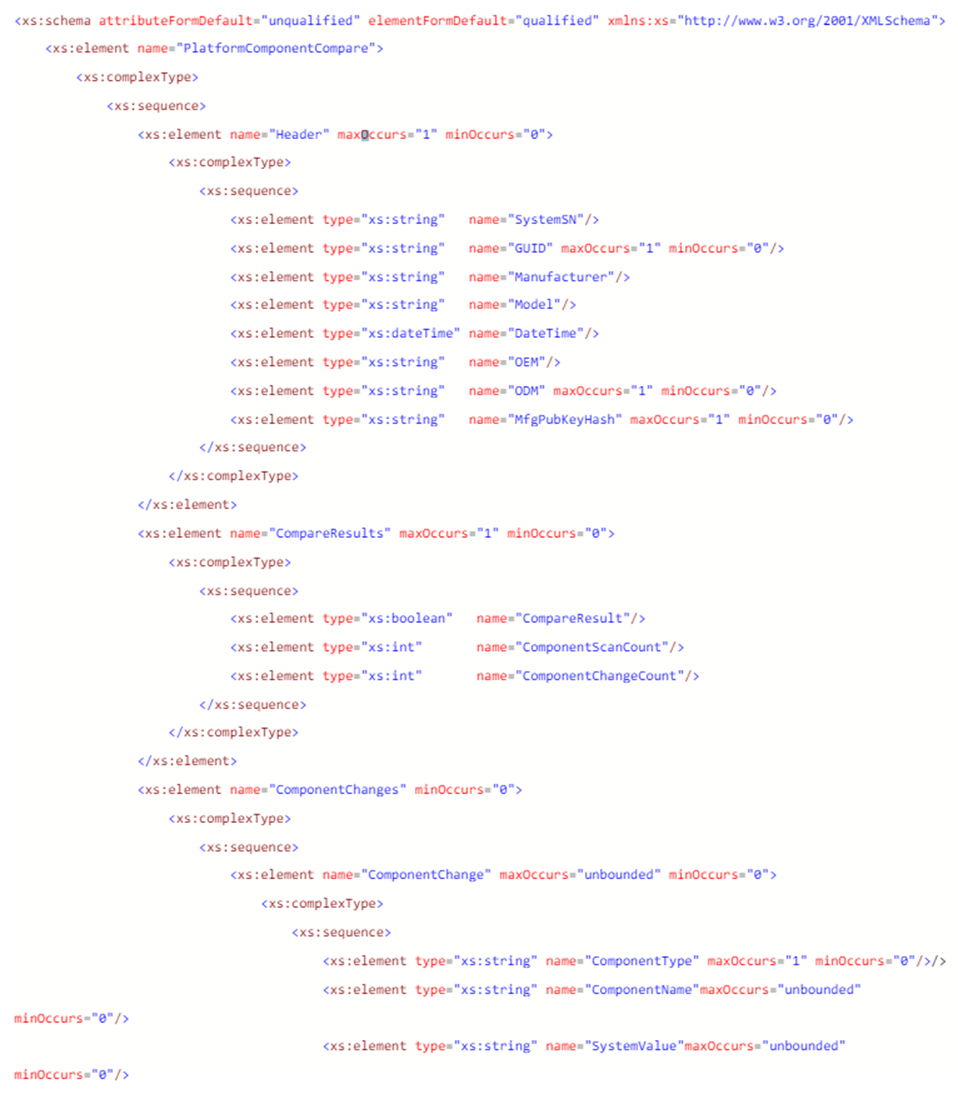
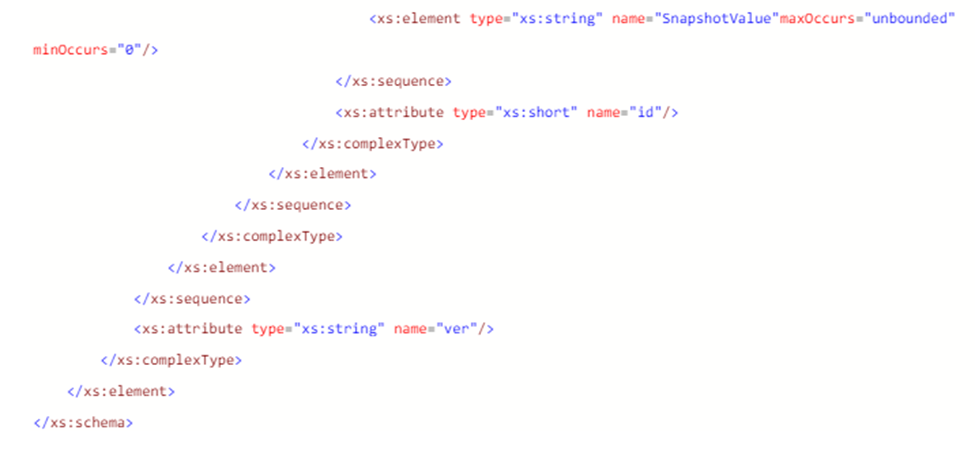
PFORMCRTCOMP: Compares the contents of the signed Platform Attribute Certificate file specified by the –in command line option to the current information from the system. It detects changes in elements like the EK Serial Number from the Trusted Platform Module and the Platform Serial Number in the system. It also compares the platform configuration from the file against the current components from the system. The results of the comparison will be displayed in the console.
The command will indicate whether changes were detected at system or component level as warning messages (in yellow).
If the result of the comparison is successful, then a success message will be displayed saying PFORMCRTCOMP PASS.
If it is not successful, then it will display PFORMCRTCOMP FAIL. It will also show the differences line by line in red.
The Platform Certificate Verify function is used to check the Platform Certificate file issued for the platform against the platform using the TPM as the hardware root of trust. The verify function will check the system manufacturer, version and serial number along with the motherboard serial number match the values in the signed platform certificate.
The Platform Certificate Verify function runs automatically when the Open button is clicked. The results are displayed in the TPM PCR Register section of the UI. If the Platform Certificate matches the system values, the message "Platform Certificate Matched" is shown, along with the certificate values.
If the Platform Certificate does not match the system values, one of two messages will be displayed:
- Platform Certificate general info did not match: This message appears when discrepancies involve general values such as the Serial Number, Model, Manufacturer, EK TPM Serial Number, or similar details.
- There are platform configuration changes: This message is shown when differences are related to platform component configurations.
All detected discrepancies will be highlighted in red.
Additionally, the command will output an error message, such as PFORMCRTCOMP FAIL, indicating that the command was unsuccessful.
Signature Verify Command
CASIGVERIFY: This command verifies the signature of the signed Platform Certificate, the signed Statement of Conformance, and the signed Direct Platform Data File. The Build Assure Issuing CA file is specified by the -ca filename, and the file to verify is selected by the -in filename.
The Platform Certificate file, the Direct Platform Data file, and the Statement of Conformance file downloaded from the Build Assure Web Portal are signed using a PKI signing process. To validate the signature of these files, an Intermediate Certificate Authority file must be downloaded.
This Intermediate Certificate Authority file contains a public key used to verify the signature of the Platform Certificate file and the Direct Platform Data file.
To download this Intermediate Certificate Authority file, visit the following URL:
Save the Intermediate Certificate Authority file on the
system for validation.
Passing signed Direct Platform Data file
When no valid signed Direct Platform Data file is being passed, the command will display an error message.
Passing signed Platform Attribute Certificate
The Platform Attribute Certificate file and the Direct Platform Data file downloaded from the TSC Web Portal are signed using a PKI signing process. To validate the signature of these files an Intermediate Certificate Authority file must be downloaded.
This Intermediate Certificate Authority file contains a public key that is used to verify the signature of the Platform Certificate file and the Direct Platform Data file.
Download the Intermediate Certificate Authority (CA) file and save it to your system. If you are unsure where to download your Issuing CA file, contact the TSC Web Portal Team for assistance in retrieving your Issuing CA.cer file.
Write Delta File Command
WRITEDELTAFILE: Allows the generation of a new delta XML file that includes only the platform components that have been added, modified, or removed from the original system setup. It compares all platform components using the current platform information by taking the base platform attribute certificate file as input and, optionally, a list of previous delta attribute certificate files.
When you have a Platform Attribute Certificate and one or more Delta Certificates, you can generate a new Delta XML file reflecting the latest system updates. To do this, add the “-deltas” flag to the previous command, followed by the filename of the Delta Certificate. If multiple Delta Certificates are used, separate their filenames with a space.
If no platform component changes are detected, the command will not generate a Delta Certificate Data file and will display an error message.
If a Platform Attribute Certificate from another system is provided, the command will not generate a Delta Certificate Data file and will display an error message.